What is Managed File Transfer (MFT)?
These days, companies are required to share a large number of files, both internally and externally.
Managed File Transfer (MFT) or Secure File Transfer (SFT), you may have heard of these technical terms to simply describe secure file transfers.
Find on this page a complete guide about MFT, its functionalities, benefits, and cost.
What is Managed File Transfer? (MFT)
These days, companies are required to share a large number of files, both internally and externally.
Managed File Transfer (MFT) or Secure File Transfer (SFT), you may have heard of these technical terms to simply describe secure file transfers.
Find on this page a complete guide about MFT, its functionalities, benefits, and cost.

A file transfer solution is often software that automates and secures transfer movements and actions via a network and a communication protocol. The security of the transfer will depend on the protocol used for communication between the computer systems. Initially, file transfers were mainly carried out in the context of Electronic Data Interchange (EDI) between systems, but soon other types of file were added to the range of data exchanged between companies.
MFT ensures file integrity even if connectivity is interrupted or if the files sent are large.
Some Managed File Transfer tools go further than simple file transfer solutions and include collaborative modules for secure email, secure document sharing, synchronisation and secure forms.
One of the first and most frequently studied aspects of Managed File Transfer solutions is security.
MFT tools support a wide range of security standards to provide functionality in line with popular regulations.
Secure file transfers protect your files both at rest and in transit, thanks to encryption technologies. Here are a few examples:

File encryption and decryption by Open PGP and Gnu PGP, using public and private keys to protect the confidentiality and integrity of your data.

Protection of files at rest using AES 256-bit encryption, so you can easily comply with security standards. Files are automatically decrypted for authorised users. Many GoAnywhere MFT features support encrypted folders.

Using SSL (Secure Sockets Layer) and TLS (Transport Layer Security) to send encrypted file transfers via AS2, FTPS and HTTPS.

Encrypted file sharing via the SFTP and SCP protocols to secure your network communications and file transfers.
Before implementing a secure file transfer solution, it is a good idea to know the basics of the protocols involved in transmission in order to remain secure. MFT solutions must be able to connect to a wide variety of file transfer servers.
The following protocols are often used :
FTP uses two separate channels for data transfers, the command channel to authenticate the user and the data channel to transfer files.
However, these two FTP channels are not encrypted, which means that the data sent is at risk of being exploited, even if it is necessary to use a user name and password to authenticate access.
Stands for FTP part SSH (Secure Shell). This is a secure FTP protocol offering an excellent alternative to insecure FTP tools or manual scripts. SFTP enables data to be exchanged via an SSH connection, offering a high level of protection for file sharing between systems, clouds, collaborators, etc.
Stands for FTP part SSH (Secure Shell). This is a secure FTP protocol offering an excellent alternative to insecure FTP tools or manual scripts. SFTP enables data to be exchanged via an SSH connection, offering a high level of protection for file sharing between systems, clouds, collaborators, etc.
Secure Copy Protocol, is an older network protocol that supports file transfers between hosts on a network. Somewhat similar to FTP, SCP supports encryption and authentication functions.
Uses TCP (Transmission Control Protocol) as a secondary protocol, which is also a stateless protocol. This means that each command is executed independently and that no session information is retained by the recipient.
HTTP/S is a stateless protocol that also uses the round-robin algorithm.
The HTTPS protocol defines the message format in which web browsers communicate and determines how a browser should respond to a web request. It is a stateless protocol, which means that each instance of communication is treated as an independent event and that no session information from previous requests is retained by the receiver.
This protocol allows each connection to the same HTTP/S server to be maintained in order to ensure the integrity of the session.
This is important because the user's HTTP/S session can generally only be managed by one HTTP/S server at a time.
PeSIT is a file transfer protocol used primarily to meet European banking standards and to transfer communications between banks in Europe.
This protocol is used to transmit confidential data reliably over the Internet. AS2 uses digital certificates and encryption standards to protect information in transit between systems and networks. AS2 messages can be compressed, signed, encrypted and sent via a secure SSL tunnel.
AS3 is a standard that can be used to transmit virtually any type of file. AS3 provides an additional level of security for data transmission through digital signatures and data encryption.
This standard enables companies to exchange data in complete security. It builds on the foundations laid by AS2, but works with web services and provides delivery notifications. As a business-to-business standard, AS4 helps to make document exchange over the Internet secure and straightforward.
Let’s take a look at the benefits of automated file transfers

Transfer automation lets you manage high volumes, while reducing or eliminating manual data processing. Automation can perform batch file transfers, while monitoring and alerting you to problems or failed transfers.
The automation features of MFT solutions offer considerable reliability and time savings. It is no longer necessary to use manual processes to move data from point A to point B. This increases file security and reduces the risk of data breaches.
Project scheduling via an integrated scheduler enables workflows to be created at different dates and times. You can schedule workflows all at once, so that they run as often as required.

Transfer automation lets you manage high volumes, while reducing or eliminating manual data processing. Automation can perform batch file transfers, while monitoring and alerting you to problems or failed transfers.
The automation features of MFT solutions offer considerable reliability and time savings. It is no longer necessary to use manual processes to move data from point A to point B. This increases file security and reduces the risk of data breaches.
Project scheduling via an integrated scheduler enables workflows to be created at different dates and times. You can schedule workflows all at once, so that they run as often as required.

Scripts are often created by developers to meet one-off file-sharing requirements, such as a report that needs to be generated every week and sent to a business partner. However, when server IPs or connection identifiers change, this becomes complicated to manage, particularly for time-poor resources. What’s more, these scripts quickly become outdated. Scripts are just a patch for a larger problem, making a centralised file sharing method included in file transfer solutions much more efficient. What’s more, scripts tend to lead to various other costly maintenance developments.
Scripts are often created by developers to meet one-off file-sharing requirements, such as a report that needs to be generated every week and sent to a business partner. However, when server IPs or connection identifiers change, this becomes complicated to manage, particularly for time-poor resources. What’s more, these scripts quickly become outdated. Scripts are just a patch for a larger problem, making a centralised file sharing method included in file transfer solutions much more efficient. What’s more, scripts tend to lead to various other costly maintenance developments.


MFT solutions generally include an integrated scheduler for project execution.
This means you can plan the desired frequency and all the relevant time and security variables for your transfer schedule.
Triggers can be defined to monitor certain events, such as the uploading or downloading of a file by a trading partner. Depending on the user-defined trigger parameters, MFT solutions can execute a variety of processes.
You will also receive email or SMS notifications of completed or failed transfers and projects.
Vous recevrez aussi des notifications par email ou SMS des transferts et projets terminés ou échoués.

MFT solutions generally include an integrated scheduler for project execution.
This means you can plan the desired frequency and all the relevant time and security variables for your transfer schedule.
Triggers can be defined to monitor certain events, such as the uploading or downloading of a file by a trading partner. Depending on the user-defined trigger parameters, MFT solutions can execute a variety of processes.
You will also receive email or SMS notifications of completed or failed transfers and projects.

High Availability (HA) refers to the ability of an IT system, application or service to remain operational and accessible to users, even in the presence of breakdowns, incidents or failures. The main objective of high availability is to ensure continuity of operations and minimise interruptions or downtime.
High availability ensures that services and systems remain operational even in the event of hardware or software failures, cyber-attacks or other technical problems. This enables businesses to maintain their operations without major interruptions, which is crucial for productivity and customer satisfaction.
By having highly available systems, downtime is reduced to a minimum. This limits financial losses, loss of productivity and negative impacts on the company's reputation.
High availability facilitates the scalability of systems and applications. It enables new resources to be added, the load to be distributed over several servers and traffic peaks to be managed efficiently without compromising availability.
In the event of a natural disaster, major incident or other unforeseen event, high availability can help ensure rapid and effective recovery of critical data and systems. Backup, replication and automatic failover mechanisms enable services to be restored quickly.
End users benefit from a better experience when systems are highly available. They can access services at any time, without interruption, which reinforces confidence in the business and increases customer satisfaction.
High Availability (HA) refers to the ability of an IT system, application or service to remain operational and accessible to users, even in the presence of breakdowns, incidents or failures. The main objective of high availability is to ensure continuity of operations and minimise interruptions or downtime.
To achieve high availability, various techniques and technologies are used, such as server redundancy, load balancing, clustering, virtualisation, backup and recovery, as well as monitoring and proactive fault management.

High availability ensures that services and systems remain operational even in the event of hardware or software failures, cyber-attacks or other technical problems. This enables businesses to maintain their operations without major interruptions, which is crucial for productivity and customer satisfaction.
By having highly available systems, downtime is reduced to a minimum. This limits financial losses, loss of productivity and negative impacts on the company's reputation.
High availability facilitates the scalability of systems and applications. It enables new resources to be added, the load to be distributed over several servers and traffic peaks to be managed efficiently without compromising availability.
In the event of a natural disaster, major incident or other unforeseen event, high availability can help ensure rapid and effective recovery of critical data and systems. Backup, replication and automatic failover mechanisms enable services to be restored quickly.
End users benefit from a better experience when systems are highly available. They can access services at any time, without interruption, which reinforces confidence in the business and increases customer satisfaction.

Regulatory compliance is an important part of MFT. Certain regulations (PCI DSS, GDPR, HIPAA, Basel, DORA, SOX, ISO 27001, FISMA & NIST, etc.) require detailed audit information to be stored and tracked. Being able to generate complete audit logs of all transfer activity and reports is therefore essential.
In addition, auditing file transfers can reinforce the confidence of business partners and customers in the security and reliability of data exchanges with the company. By demonstrating that the company has put in place robust security and compliance measures for file transfers, it can reassure its partners and customers that their sensitive data is being protected. This can help to strengthen business relationships, maintain the company’s reputation and avoid the risk of litigation or loss of partners or customers due to data security concerns.
Regulatory compliance is an important part of MFT. Certain regulations (PCI DSS, GDPR, HIPAA, Basel, DORA, SOX, ISO 27001, FISMA & NIST, etc.) require detailed audit information to be stored and tracked. Being able to generate complete audit logs of all transfer activity and reports is therefore essential.
In addition, auditing file transfers can reinforce the confidence of business partners and customers in the security and reliability of data exchanges with the company. By demonstrating that the company has put in place robust security and compliance measures for file transfers, it can reassure its partners and customers that their sensitive data is being protected. This can help to strengthen business relationships, maintain the company’s reputation and avoid the risk of litigation or loss of partners or customers due to data security concerns.

Cost of a Managed File Transfer Solution

The cost of a Managed File Transfer (MFT) solution varies considerably depending on a number of factors, including the size of the business, the volume of file transfers, the functionality required and the specific configuration.
In general, the cost of a professional MFT solution can vary from a few thousand euros to several tens of thousands of euros per year, depending on the company’s needs. Here are a few things to bear in mind when estimating costs:
The price of a file transfer solution

The cost of a Managed File Transfer (MFT) solution varies considerably depending on a number of factors, including the size of the business, the volume of file transfers, the functionality required and the specific configuration.
In general, the cost of a professional MFT solution can vary from a few thousand euros to several tens of thousands of euros per year, depending on the company’s needs. Here are a few things to bear in mind when estimating costs:
You will generally need to purchase software licences to use the MFT solution. The cost of licences may vary depending on the number of users, servers, nodes, etc.
Installing, configuring and integrating the solution into your existing environment may entail additional costs, particularly if you require professional assistance.
Maintenance and support costs are generally invoiced annually as a percentage of the initial cost of the licence. This can vary from 15% to 25% or more.
Some MFT solutions charge according to the volume of file transfers or the number of transactions, which means that the more files you transfer, the higher the costs may be.
If you require advanced functionality such as workflow management, enhanced security, regulatory compliance or customised integrations, this can lead to additional costs.
If you choose a cloud-based MFT solution, costs can vary depending on the monthly or annual subscription.
Secure file transfer software is a crucial tool for businesses and individuals seeking to exchange sensitive information while safeguarding data integrity and confidentiality.
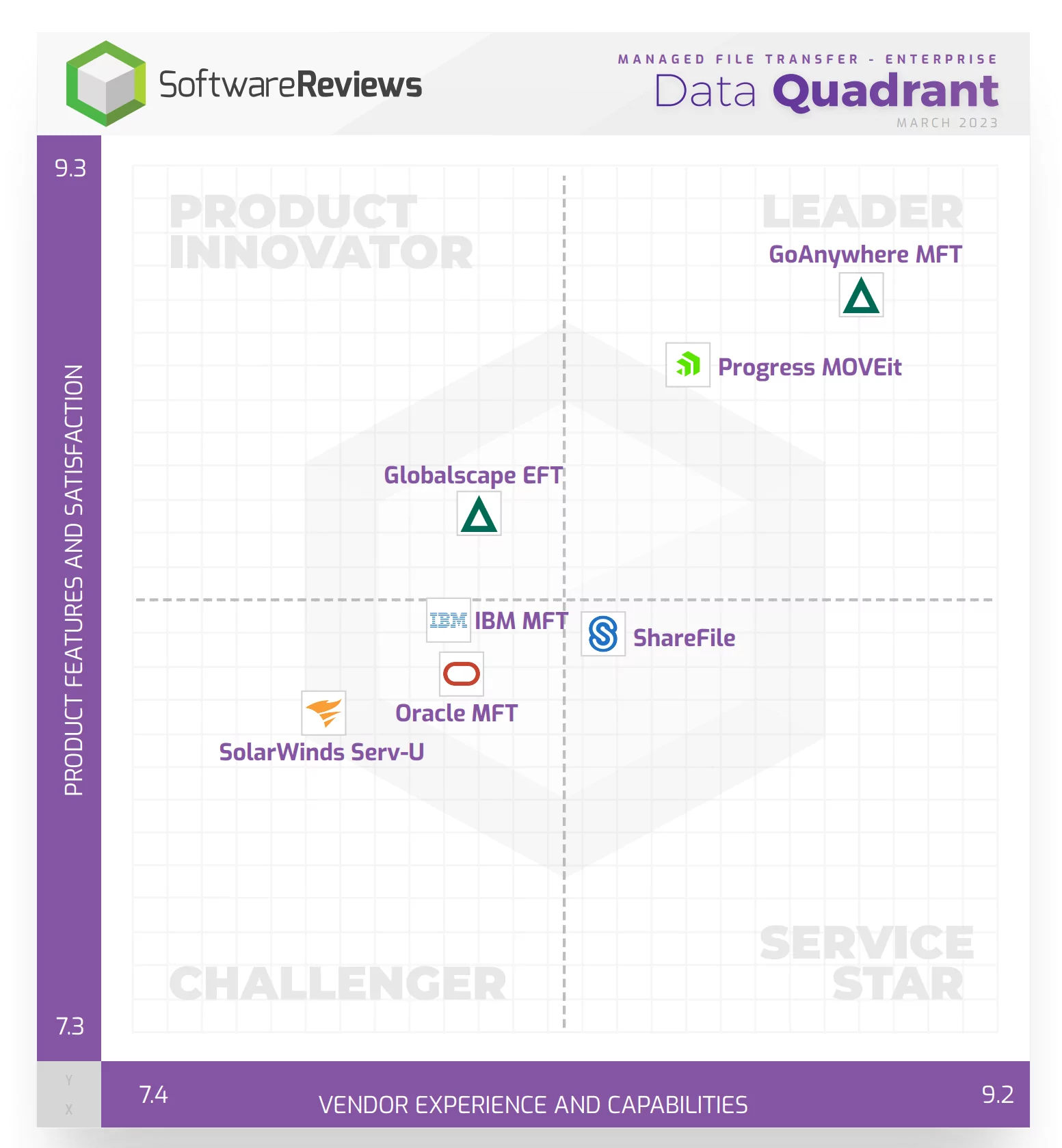
GoAnywhere is one of these MFT leading market solution.
GoAnywhere MFT employs advanced encryption protocols to ensure that files remain secure during transit, protecting them from unauthorized access and potential cyber threats.
GoAnywhere incorporate automation and secure protocols such as SFTP (Secure File Transfer Protocol) or FTPS (FTP Secure), AS2, AS4, etc. to establish a protected channel for data transmission.
Moreover, GoAnywhere provides comprehensive audit trails and reporting capabilities. These features enable users to track file movements, monitor user activities, and generate reports for compliance purposes, helping organisations adhere to regulatory requirements and internal security policies.
How our experts can assist you to create your own MFT experience? 🙂
Talk to one of our experts for 15 minutes or so and tell us all your questions about MFT.
Make an appointment now and whenever you like!
Headquarters and Office
Laan van Zuid Hoorn 60
2289 DE Rijswijk
NETHERLANDS
Technical Office
44 rue de France
88300 Neufchâteau
FRANCE
Sales Office – PAE Les Glaisins
14 rue du Pré Paillard
74940 Annecy
FRANCE
Technical Office
27 Avenue de l’Opéra
75001 Paris
FRANCE
Contact
sales@bluefinch-esbd.com
Netherlands: +31 (0)8 82 58 33 46
France: +33 (0)9 70 75 61 13
Sitemap
We use cookies to optimise your experience & our services on the website. Nous utilisons des cookies pour optimiser votre expérience et nos services.
Join us on May 22 and 23 at the Stockholm Tech Show, stand J02.
One of the most eagerly awaited technology events of the year in the Nordics!
Interested in attending conferences during the event? Ask for one of our free passes* and save 450€.
